The Global Risk of XSS Attacks

This cybersecurity report analyzes Operation RoundPress, a sophisticated cyber-espionage campaign conducted by Russian state-sponsored group APT28 that exploited cross-site scripting (XSS) vulnerabilities in popular webmail platforms to steal sensitive communications from government and defense entities across Eastern Europe, South America, and Africa—particularly those supporting Ukraine. The report highlights how XSS attacks have evolved from basic web vulnerabilities into advanced intelligence-gathering tools enhanced by AI-generated payloads, demonstrating the growing threat posed by state-sponsored actors who are increasingly weaponizing traditional web application flaws for geopolitical espionage.
Overview
Cross-site scripting (XSS) is a longstanding and critical web application vulnerability that continues to evolve in complexity and impact. Originating in the late 1990s, XSS has become a powerful tool for cyber threat actors to inject malicious scripts into trusted websites, enabling data theft, session hijacking, and unauthorized actions within user browsers. This report outlines the historical development of XSS, and categorizes its three main variants: Reflected, Stored, and DOM-based. This report also explains common infection vectors and technical attributes with an emphasis placed on the modern threat landscape, where AI-generated payloads and adaptive techniques are increasing the potency and evasiveness of XSS attacks.
A focal point of the analysis is Operation RoundPress, a recent cyber-espionage campaign conducted by APT28, a Russian state-sponsored threat actor. The operation exploited XSS vulnerabilities in popular webmail platforms to exfiltrate sensitive government and defense-related communications across Eastern Europe, South America, and Africa. By detailing the technical methods, exfiltrated data, and geopolitical implications of this campaign, the paper underscores the persistent threat XSS poses to national security. The final sections present strategic insights, recommendations, and forward-looking projections on how artificial intelligence and quantum computing are reshaping both offensive and defensive XSS capabilities.
Key Findings:
- XSS has evolved into a sophisticated tool for cyber-espionage, especially by state-sponsored actors like APT28.
- Operation RoundPress demonstrates how XSS can compromise webmail platforms and exfiltrate sensitive data across multiple regions.
- AI is now being used to generate dynamic, evasive XSS payloads and automate large-scale exploitation.
- XSS is increasingly part of multi-stage attacks involving credential theft, lateral movement, and session hijacking.
- Future threats include AI-adaptive payloads and quantum-driven encryption bypasses, requiring proactive and evolving defenses.
1.0 XSS Origin and Evolution
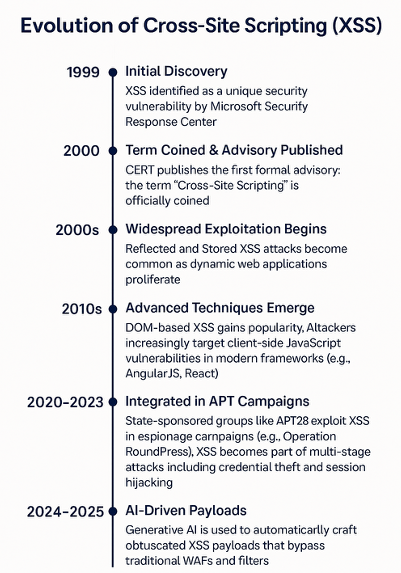
1.1 Technical Attributes
There are many different ways for threat actors to exploit XSS, but there 3 main types of XSS attacks that are still prevalent to this day.
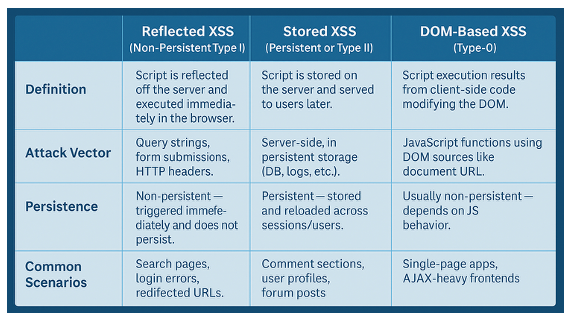
1.2 Common Infection Vectors
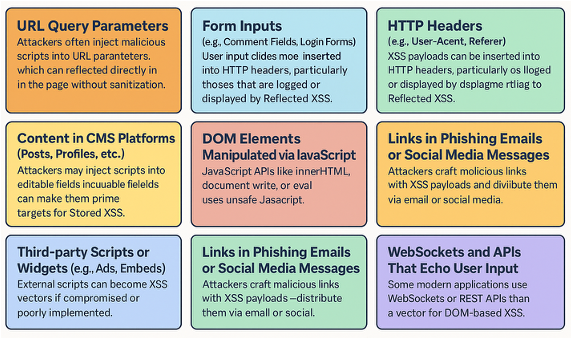
1.3 Evolving Tactics
With AI constantly changing the threat landscape, it would make sense that attackers will also be utilizing AI to help craft more sophisticated XSS payloads to bypass current defenses implemented against XSS.
Crafting XSS payloads relied heavily on manual effort and known patterns, but with AI, attackers can automate the creation of dynamic, obfuscated payloads tailored to bypass specific web application firewalls (WAFs) and content security policies. These AI-driven tools can generate a wide variety of syntactic variations in real time, test them against live defenses, and iterate rapidly based on what successfully evades detection.
AI can also assist in identifying potential injection points in applications by analyzing web traffic, source code, or API behaviors more efficiently than manual reconnaissance. Some research tools and proof-of-concept frameworks even simulate adversarial behavior, using AI to "learn" how a target's security mechanisms respond to different inputs, enabling the generation of adaptive payloads that evolve during the attack process. This marks a significant shift in the threat landscape, turning XSS from a relatively simple vulnerability into a more dynamic and evasive threat that requires equally adaptive defenses.
2.0 Case Study: Operation RoundPress
Operation RoundPress is a cyber-espionage campaign attributed to APT28—also known as Fancy Bear, Sednit, Sofacy, or Forest Blizzard—a Russian state-sponsored hacking group active since at least 2004. They are most notoriously well-known in the United States for the Democratic National Committee hack in 2016, in which they breached the democratic parties emails. Operation Roundpress was first uncovered by ESET researchers in May 2025, the operation has been ongoing since at least 2023 and reflects APT28’s continued focus on geopolitical intelligence gathering. For a detailed account of APT28’s activities, refer to the timeline of events provided below.
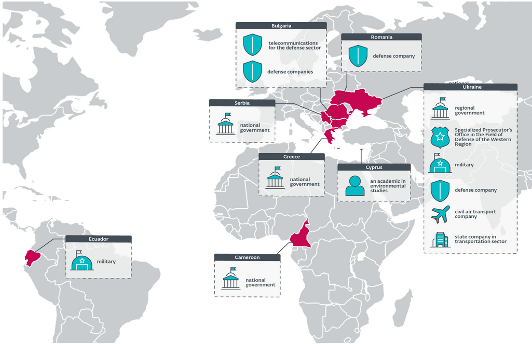
In this campaign, APT28 targeted government and defense-related entities, with a primary focus on Ukrainian governmental organizations and defense companies in Bulgaria and Romania. The operation also extended to select targets in Africa, Europe, and South America. Many of the defense companies targeted were involved in the production or supply of Soviet-era weaponry, much of which is being used in the ongoing Ukraine conflict. As illustrated in the graphic, these represent the regions known to have been targeted by APT28.
2.1 Timeline of Events
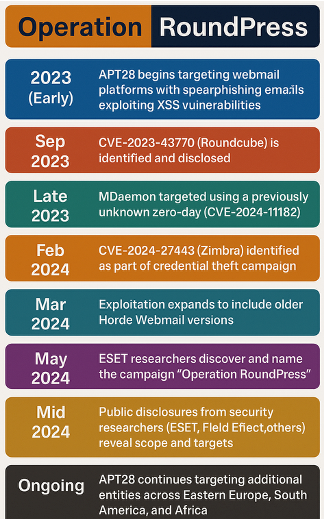
2.2 Technical Attack Vector Analysis
In 2023–2024, the Russian state-sponsored group APT28 (also known as Fancy Bear or Sednit) launched a targeted spear phishing campaign known as Operation RoundPress, exploiting XSS vulnerabilities in widely used webmail platforms—specifically Roundcube, Horde, MDaemon, and Zimbra. These attacks highlight the evolution of XSS from a relatively basic web vulnerability into a sophisticated weapon for espionage.
Infection Vector: XSS via Spear Phishing Emails
APT28’s primary attack vector involved embedding malicious JavaScript in the body of spear phishing emails. When unsuspecting users opened these messages in vulnerable webmail clients, the scripts executed automatically, bypassing endpoint protections and web content filters.
Notably, these attacks relied on the fact that many webmail applications render HTML email content without sufficient sanitization, which is particularly dangerous when JavaScript is injected into fields like the sender name, subject line, or body content.
Exploited Vulnerabilities
APT28 combined the use of known CVEs with novel, likely zero-day vulnerabilities:
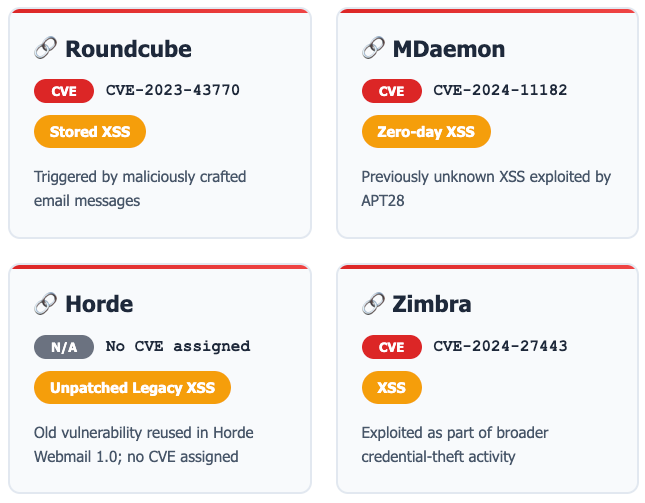
Attack Techniques
- Phishing Lures Posing as News Media: Emails were designed to mimic legitimate news organizations, lending credibility to the message and increasing the likelihood of victim interaction.
- Custom JavaScript Malware (SpyPress): Payloads like SpyPress.ROUNDCUBE and SpyPress.MDAEMON harvested session data, inbox contents, and address books, and sometimes attempted 2FA bypass.
2.3 Impact Analysis
Operation RoundPress, orchestrated by the Russian state-sponsored group APT28 (also known as Fancy Bear or Sednit), has had significant operational, strategic, and geopolitical impacts. The campaign's exploitation of XSS vulnerabilities in widely used webmail platforms has compromised sensitive communications and highlighted vulnerabilities in cybersecurity practices.

Organizations must remain vigilant in the face of ongoing spear phishing campaigns like Operation RoundPress. The exploitation of seemingly routine webmail vulnerabilities through advanced techniques—weaponized XSS payloads and zero-day exploits—underscores the persistent and evolving nature of modern cyber threats.
Any unauthorized access to sensitive government or defense-related communications poses a direct threat to national security. The exfiltration of login credentials, session cookies, and unencrypted email content provides adversaries with the ability to impersonate officials, gain persistent unauthorized access, and harvest classified intelligence. This not only compromises the confidentiality of critical operations but also opens the door to follow-on attacks like disinformation campaigns, espionage, or sabotage.
The reputational and legal consequences of such breaches can be severe. Affected organizations may face regulatory investigations, erosion of public trust, and increased scrutiny from domestic and international partners. In high-stakes sectors like defense and foreign policy, these repercussions can be as damaging as the technical breach itself.
3.0 Campaign Comparison
Another campaign with striking similarities to the current campaign was the Winter Vivern email campaign. Winter Vivern Is and Russian/Belarusian affiliated APT that has also been targeting espionage campaigns towards countries who have been supporting Ukraine's war effort. They mainly targeted telecommunication organizations that support the Ukraine effort. Similarly to the current Operation Roundpress, they have also exploited a zero-day vulnerability within Roundcube Webmail, while also using phishing websites, malicious documents, and a custom-made PowerShell backdoor.
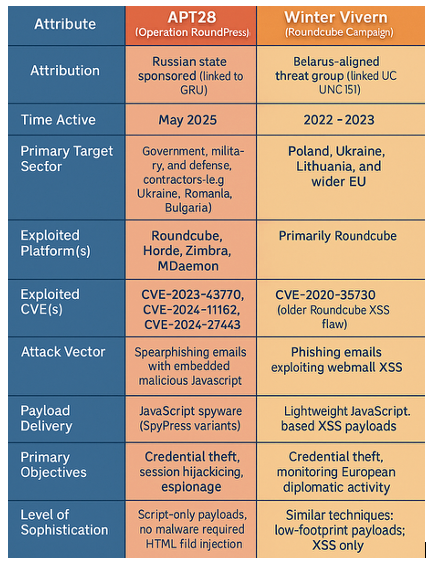
Comparing the two campaigns, Many Russian affiliated APT groups have been targeting any organizations have consistently targeted organizations within countries that publicly support Ukraine in the ongoing war. Both groups have demonstrated a clear operational focus on government, defense, and diplomatic entities, using tailored spear phishing tactics to gain access to sensitive communications.
The repeated use of XSS as the initial attack vector in both campaigns underscores a troubling trend: sophisticated threat actors are increasingly leveraging overlooked client-side vulnerabilities to silently compromise high-value targets. This should serve as a critical warning to all organizations, particularly any of those aligned with Ukrainian interests should focus on defensive controls, including input validation, email sanitization, and webmail hardening, are essential to counter these evolving threats.
3.1 Strategic Implications
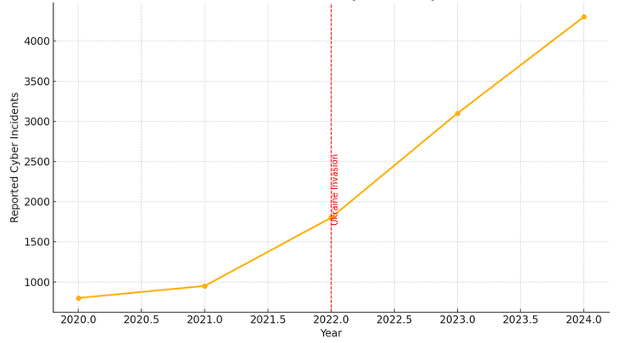
The escalation in Russian cyber operations post-2022 highlights the need for heightened cybersecurity measures, especially for nations and organizations aligned with Ukraine, particularly in Government and Telecommunications. Proactive defense strategies, international collaboration, and continuous monitoring are essential to mitigate the risks posed by state-sponsored cyber threats.
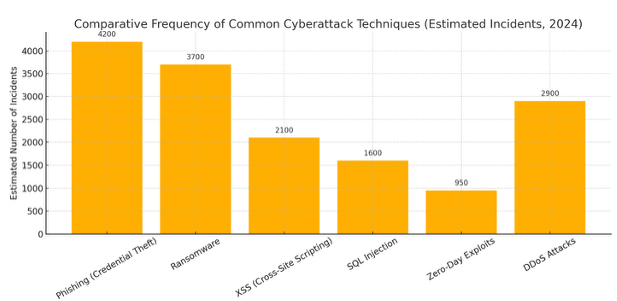
This graph highlights just how prevalent XSS has become in the modern threat landscape. In many real-world scenarios, XSS does not occur in isolation—it is often compounded with other attack vectors, as demonstrated in Operation RoundPress, where it was used to facilitate credential theft, session hijacking, and persistent access.
According to the OWASP Foundation, over 94% of web applications they have tested exhibit some form of injection vulnerability, with XSS being one of the most common. Additionally, the 2024 Verizon Data Breach Investigations Report (DBIR) emphasizes that web application attacks remain among the top breach vectors, particularly in environments lacking proper input validation and output encoding.
These trends underscore the urgent need for organizations to implement strong mitigation strategies. These should include secure coding practices, content security policies (CSP), webmail hardening, and continuous vulnerability scanning. As XSS continues to evolve alongside advanced persistent threats, proactive defense is no longer optional.
4.0 Recommendations
- Contextual Output Encoding: Encode all user-supplied content based on the output context (HTML, JavaScript, URL, etc.) to prevent script execution.
- Strict Input Validation: Use allowlist validation to restrict acceptable input types and reject or sanitize potentially malicious input.
- Content Security Policy (CSP): Deploy a strong CSP header to limit the sources of executable scripts and block inline code by default.
- Sanitize HTML with Trusted Libraries: Use libraries like DOMPurify to clean and filter any user-generated HTML or rich text before rendering.
- Avoid Dangerous JavaScript Functions: Refrain from using functions like
eval(),innerHTML, anddocument.write()with user input, as they are common vectors for XSS.
5.0 Future XSS Trend Projections
5.1 Artificial intelligence
- Offensive Use: Cybercriminals are leveraging generative AI to craft sophisticated XSS payloads capable of bypassing traditional WAFs. For instance, the GenXSS framework employs large language models to generate complex XSS attacks, with a significant success rate in evading standard WAF protections.
- Defensive Use: Conversely, defenders are adopting AI-driven tools to enhance detection capabilities. Machine learning models trained on obfuscated XSS patterns have demonstrated improved accuracy in identifying and mitigating such threats.
- Automation of XSS attacks: Attackers are developing automated tools that can identify and exploit XSS vulnerabilities at scale, increasing the speed and reach of such attacks.
- Adaptive Threats: AI-powered attacks can adapt in real-time to bypass security measures, making traditional defense mechanisms less effective.
5.2 Quantum Computing and Cryptographic Implications
The introduction of quantum computing presents many challenges to cybersecurity, but particular to XSS
- Cryptographic Vulnerabilities: Quantum computers have the potential to break current encryption standards, which could indirectly affect XSS attack vectors by compromising secure communications and data integrity. Organizations like Microsoft have already publicly disclosed that they have successfully Invented a "Quantum chip" and organizations must be ready to adapt to potential vulnerabilities that become more widespread because of quantum processing.
6.0 Hunter Insights
Operation RoundPress represents a concerning evolution in state-sponsored cyber operations, demonstrating APT28's continued adaptation of traditional web vulnerabilities for strategic intelligence collection against Ukraine-aligned targets. The campaign's technical sophistication—leveraging zero-day XSS exploits in enterprise webmail platforms combined with custom JavaScript malware (SpyPress variants)—indicates Russian cyber capabilities are increasingly focused on client-side attack vectors that bypass traditional network defenses. Most significantly, the integration of AI-generated, adaptive XSS payloads signals a paradigm shift toward automated, evasive exploitation techniques that will likely proliferate across the APT ecosystem within 12-18 months. Looking forward, we assess with high confidence that XSS attacks will become increasingly weaponized by nation-state actors, particularly as AI democratizes payload generation and quantum computing threatens current cryptographic protections. Organizations supporting Ukraine or operating in contested geopolitical environments should anticipate sustained targeting through similar webmail exploitation campaigns, while the broader threat landscape will likely see XSS evolve from opportunistic attacks to precision intelligence collection tools requiring fundamentally new defensive approaches focused on runtime protection and AI-enhanced detection capabilities.





