Evolution of BERT Ransomware

BERT ransomware, first identified in April 2025, has rapidly evolved from targeting only Windows systems to launching sophisticated cross-platform attacks against Linux environments, primarily through phishing campaigns that infiltrate critical infrastructure across healthcare, manufacturing, logistics, and IT sectors in multiple countries including the U.S., U.K., and Asia. The ransomware group employs advanced techniques including PowerShell-based security evasion, multiple encryption algorithms, and shares 80% of its codebase with the REvil ransomware family, typically demanding around 1.5 BTC while causing significant operational disruptions and data exfiltration through dark web negotiation platforms.
Overview
BERT ransomware, initially targeting Windows systems, has significantly expanded its capabilities to include Linux environments. First identified in April 2025, BERT has rapidly evolved from focusing solely on Windows to launching cross-platform attacks against critical infrastructure, particularly in enterprise settings. The ransomware’s primary infection vector is phishing, utilizing social engineering techniques to infiltrate systems. This evolution marks a significant shift in the threat landscape, as Linux systems, traditionally seen as less vulnerable, are now under attack. The malware’s complexity includes weaponized Executable and Linkable Format (ELF) files for Linux machines, and its attack mechanisms involve sophisticated strategies, including disabling security controls and leveraging a mix of encryption algorithms for data exfiltration.
The BERT ransomware group has successfully compromised organizations across multiple sectors, with the United States, the United Kingdom, Malaysia, Taiwan, Colombia, and Turkey being some of the most affected regions. Key industries include service, Manufacturing, Logistics, IT, and Healthcare. In addition to its technical evolution, the group has established a dark web presence with leak sites and negotiation platforms, indicating a long-term operational strategy focused on extortion. The ransom demands typically range around 1.5 BTC, with varying amounts based on the target’s size and perceived ability to pay. The sophisticated use of PowerShell scripts to disable security mechanisms before deploying the payload highlights the growing complexity of ransomware attacks.
Key Findings:
- BERT ransomware initially targeted Windows systems but has expanded to include Linux machines, posing a significant threat to enterprise infrastructures that rely on Linux servers.
- Phishing remains the primary infection vector, with social engineering techniques being employed to gain initial access to networks.
- The group uses weaponized ELF files for Linux systems, sharing 80% of its codebase with the Revil (Sodinokibi) ransomware family.
- Ransomware samples are hosted on dark web platforms and serve as negotiation points for extortion.
- The group employs sophisticated attack sequences, including disabling Windows security controls using PowerShell scripts before executing the payload.
- The most affected industries include Manufacturing, Logistics, IT, and Healthcare, with major victims in the United States, the United Kingdom, Malaysia, Taiwan, Colombia, and Turkey.
- The ransom demand averages around 1.5 BTC, with the amount varying based on the victim’s size.
1.0 Ransomware Overview
1.1 Initial Discovery and Detection
BERT ransomware was first detected in April 2025 but had already been active since mid-March 2025. Initially, it targeted Windows systems, but by May 2025, it had expanded to include Linux servers, a significant shift in its operational scope. The discovery followed the identification of weaponized ELF files designed specifically for Linux machines. The malware is delivered through phishing campaigns, typically utilizing social engineering to trick victims into executing malicious payloads.
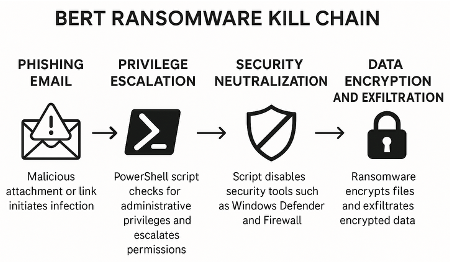
1.2 Infection Chain and Payload Execution
BERT's infection process begins with phishing emails containing malicious attachments or links. Upon execution, the malware initiates a multi-step infection process:
- Privilege Escalation: On Windows systems, a PowerShell script checks for administrative privileges and escalates permissions as needed.
- Security Neutralization: The script disables security tools, including Windows Defender, Firewall, and User Account Control (UAC), via registry modifications.
- Payload Execution: After neutralizing security defenses, the script downloads and executes the ransomware payload from a remote server.
- Data Encryption and Exfiltration: The ransomware encrypts files using AES, RC4, Salsa20, and ChaCha algorithms. It also exfiltrates encrypted data to attacker-controlled infrastructure.
1.3 Attack Vector and Delivery Methods
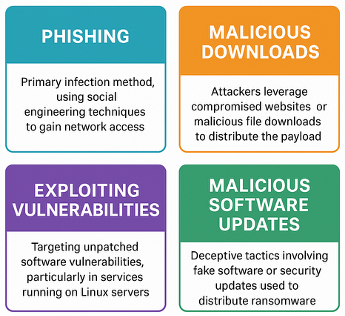
1.4 Infection Chain and Payload Execution
1.5 Weaponization and Encryption Mechanism
BERT employs sophisticated encryption mechanisms. The Windows variant uses RSA encryption, while the Linux variant uses a combination of AES, RC4 PRGA, Salsa20, and ChaCha. The Linux variant also shares 80% of its codebase with the REvil ransomware family, indicating the reuse of established attack techniques. Data exfiltration is carried out using Base64 encoding, which ensures that the stolen data is obfuscated.
2.0 Threat Actors Using BERT
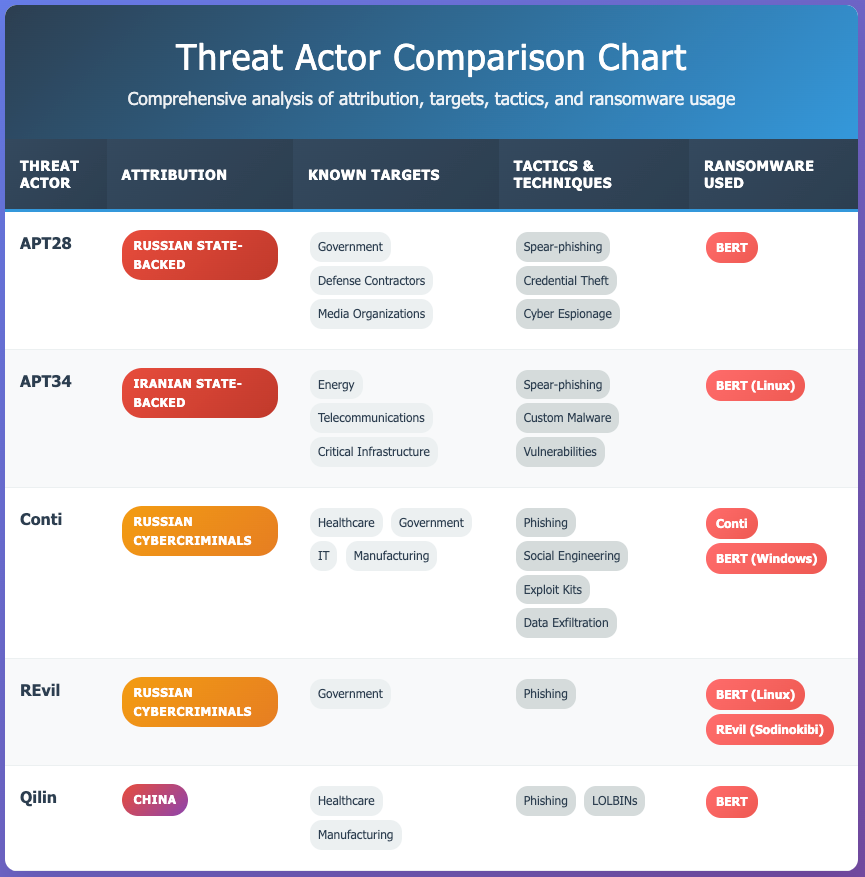
3.0 Real World Use Cases
3.1 Attack on a U.S-based Manufacturing Company
In a notable attack against a major manufacturing firm in the U.S, BERT ransomware infiltrated the organization’s network through a spear-phishing email. SIMCO Electronics, a U.S.-based provider of calibration and software solutions, was attacked by BERT ransomware on April 30, 2025. The attack led to the leak of internal data, including sensitive company information. This incident underscores the vulnerability of manufacturing firms to cyber threats. The email, disguised as a legitimate security update, contained a malicious attachment that, once executed, deployed the ransomware. Once inside, the malware encrypted critical design files and production data, halting the manufacturing process. The ransom demand was set at 1.5 BTC, causing significant financial loss and operational disruption for the company.
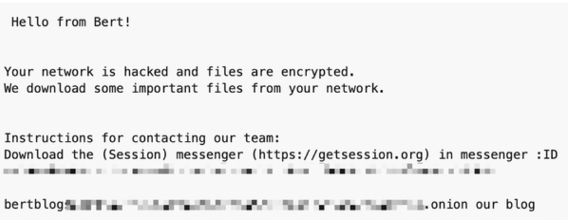
3.2 Attack on UK-based Healthcare Provider
A healthcare provider in the UK was targeted by BERT ransomware, causing disruption in medical services. Synnovis, a laboratory services provider to NHS hospitals in London, suffered a ransomware attack in June 2024. The attack disrupted critical medical services, including blood transfusions and emergency departments, and led to the cancellation of thousands of medical procedures. The group Qilin claimed responsibility for the attack. The attack started with phishing emails that tricked employees into opening infected attachments. Patient records, including sensitive personal and health data, were encrypted and exfiltrated. The group demanded 1.5 BTC for decryption, and the attack disrupted critical healthcare services for several days. The breach also led to concerns about patient confidentiality and compliance with healthcare regulations like GDPR.
3.3 Attack on Logistics Company in Taiwan
A logistics company in Taiwan was struck by BERT ransomware, which crippled its shipment tracking system. All Ring Tech Co., Ltd., a Taiwanese company specializing in automation equipment for semiconductors, LEDs, and solar technology, was attacked by BERT ransomware on May 16, 2025. The attack resulted in the leak of internal data, highlighting the risks faced by logistics and technology firms. The ransomware entered through a phishing campaign targeting administrative staff. Once deployed, it encrypted shipping and inventory data, effectively halting operations. This attack delayed shipments across Asia, highlighting the vulnerability of logistics providers, which rely heavily on digital infrastructure for timely deliveries.
4.0 Post-Compromise Risks and Impact
The post-compromise risks of a BERT ransomware attack are particularly damaging for organizations, with long-term consequences that go beyond standard data encryption. When sensitive data—patient records, intellectual property, and proprietary business strategies—is exfiltrated, it can be sold on the dark web or used for further extortion. This significantly increases the financial toll, as ransom demands are often high, and failure to pay results in permanent data loss and widespread business disruption. Industries like Healthcare, Logistics, and Manufacturing are hit especially hard, as the encrypted data often includes critical operational information that is necessary for daily functions. For instance, a healthcare provider could see disruptions in patient care or the cancellation of medical procedures, leading to not only financial losses but also regulatory scrutiny, especially with healthcare-specific regulations like GDPR or HIPAA. Such attacks can result in compliance violations, legal penalties, and significant reputational damage.
Reputation and market standing are severely impacted, particularly for organizations in high-profile sectors like Healthcare and Government. When these industries are affected, customer trust erodes, and regulatory bodies may impose stricter oversight, leading to lost business and client attrition. Moreover, BERT’s capability to exfiltrate intellectual property could cause irreparable harm to organizations involved in research and development, as proprietary data, trade secrets, and manufacturing designs are stolen and potentially exploited by competitors. The supply chain disruption caused by BERT is also a significant risk, as encrypted operational data, including shipment tracking and production details, can completely halt operations. This has a cascading effect, crippling not just the target company but also its partners, suppliers, and clients. As a result, the attack can lead to prolonged logistical delays and financial instability across the entire supply chain, impacting global operations and causing long-term damage that is difficult to recover from.
5.0 Technical Analysis
BERT ransomware stands out for its advanced technical capabilities, utilizing sophisticated methods to bypass security and ensure its payload is executed. On Windows systems, BERT employs PowerShell scripts to escalate privileges, disable Windows Defender, and stop firewall services, ensuring the ransomware operates without interference. This technique is common among advanced groups like REvil and Conti. For Linux systems, BERT shares 80% of its code with REvil and uses multiple encryption algorithms (AES, RC4 PRGA, Salsa20, ChaCha) to lock files. The Linux variant uniquely leverages AWK commands for registry queries and Base64 encoding for obfuscation, enabling it to evade detection. BERT targets both Windows (versions 7, 8, 10) and Linux (versions 4.x, 5.x) systems, marking its expansion into critical infrastructure environments. Additionally, it utilizes encrypted C2 communication through Russian-controlled infrastructure and onion sites for data leaks and ransom negotiations, complicating efforts to track or disrupt the group. The ransomware also uses unusual file extensions like "encryptedbybert" and "encryptedbybert3" to avoid detection by traditional antivirus tools.
BERT Ransomware Technical Comparison
Comparative Analysis of Advanced Ransomware Families
| Technical Feature | BERT | REvil | Conti |
|---|---|---|---|
| Payload Delivery |
PowerShell scripts Windows Defender bypass Firewall service termination Privilege escalation |
Exploit kits Supply chain attacks RDP exploitation |
PowerShell scripts Cobalt Strike TrickBot partnership |
| Code Origin |
80% REvil code base Custom modifications |
Original codebase Continuous evolution |
Original development Ryuk successor |
| Encryption Methods |
AES
RC4 PRGA Salsa20 ChaCha |
AES
RC4 PRGA Salsa20 ChaCha |
AES-256 RSA-4096 |
| C2 Infrastructure |
Russian-controlled servers Encrypted communication Onion sites for negotiation |
Decentralized infrastructure Tor-based communication Happy Blog leak site |
Cobalt Strike beacons Encrypted channels Conti News leak site |
| Target Systems |
Windows Linux (AWK commands) Base64 obfuscation |
Windows Linux ESXi |
Windows Network shares Domain controllers |
| File Extension |
.encryptedbybert .encryptedbybert3 |
Random alphanumeric Varies by campaign |
.CONTI Campaign-specific |
6.0 Recommendations for Mitigation
6.1 Implement Comprehensive Endpoint Detection and Response (EDR) Solutions:
- EDR Solution: Deploy advanced EDR solutions that focus on detecting malicious behaviors like privilege escalation, disabling security controls, and unusual network traffic indicative of ransomware activity.
6.2 Enforce Privilege Management and User Behavior Analytics:
- Least Privilege Access (LPA): Restrict administrative access to systems and applications and enforce role-based access controls (RBAC).
- Advanced User Behavior Analytics (UBA): Utilize UBA tools to detect abnormal user actions, like logging in from unfamiliar locations or accessing sensitive files.
6.3 Harden Linux and Windows Systems:
- Linux Security: Implement strong security controls on Linux systems, including file integrity monitoring and proper user access management.
- Windows Security: Ensure all security features like Windows Defender, UAC, and Firewall are configured and actively monitored.
6.4 Improve Phishing Detection and User Awareness Training:
- Anti-Phishing Tools: Deploy machine learning-based email filtering solutions to detect phishing attempts.
- User Education: Regularly conduct security awareness training to help users recognize phishing attempts and malicious attachments.
6.5 Conduct Regular Vulnerability Scanning and Patch Management:
- Scans: Regularly scan for vulnerabilities in both Windows and Linux environments and applying patches promptly. Many attacks, including those involving BERT, leverage unpatched vulnerabilities to gain initial access.
7.0 Hunter Insights
Analytical Assessment & Future Predictions
BERT ransomware represents a concerning evolution in the threat landscape, demonstrating rapid cross-platform expansion from Windows-exclusive targeting to sophisticated Linux capabilities within a two-month timeframe while leveraging 80% code overlap with the established REvil ransomware family to inherit proven attack methodologies. The group's strategic focus on critical infrastructure sectors (Healthcare, Manufacturing, Logistics) across six countries, combined with their use of encrypted C2 infrastructure, onion-based negotiation platforms, and advanced PowerShell-based security evasion techniques, indicates a well-resourced and operationally mature threat actor. Future predictions suggest BERT will likely expand its geographic footprint beyond current target regions, increase ransom demands as victims demonstrate a willingness to pay 1.5 BTC amounts, and potentially adopt a RaaS model given the technical sophistication and proven attack chain effectiveness. The group's rapid technical evolution from Windows-only to cross-platform capabilities within 60 days signals they will likely incorporate additional operating systems and cloud environments into their targeting scope, while the documented success against high-value targets in regulated industries a suggests continued focus on organizations with both high payment capacity and critical operational dependencies that make them more likely to capitulate to extortion demands.





