Binding Operational Directive 23-01: Improving Asset Visibility and Vulnerability Detection on Federal Networks
How it applies to Industrial Automation and Control Systems (IACS) and Operational Technology (OT) Control Systems

Binding Operational Directive 23–01 — Improving Asset Visibility and Vulnerability Detection on Federal Networks
How it applies to Industrial Automation and Control Systems (IACS) and Operational Technology (OT) Control Systems
This directive’s aim is two folds:
1- Force the Information Technology (IT) community to take responsibility for the assets’ discovery of IP-based devices, and
2- Determine if an asset has a vulnerability that is unpatched and be responsible for patching it.
Though this is one of the first considerations in any good cybersecurity plan, not all IT groups apply it following a mature model, and some apply it in a destructive way when it comes to IACS/OT networks.
In an IACS/OT network, follow the NIST SP 800–82 (latest rev. Currently rev 2) and implement an assets discovery method for all your IP-networked devices using passive scanning only. You need to do such a scan once a week or less depending on the design that you use for your IACS network: If you segregate (read can be physically disconnected for any other network, including the Enterprise network) correctly your IACS/OT network and use fixed IP, then you can afford to scan once every week or two without losing sight of the reason you perform this scan! That includes identifying the make and model of the devices and finding out the “end-of-life” of each, in order to plan for replacements.
If you are implementing a Purdue Model with proper segmentation and micro-segmentation (Zones and Conduits) between the different Purdue levels, then you would be following the directive’s requirements by keeping two separate assets lists for the Purdue Level 3 and for the Purdue Levels 0, 1 & 2.
Adding a physical firewall between Purdue Level 3 and above (Level 3.5 — DMZ and Level 4+ — Enterprise) will address one aspect of the IACS/OT systems Zero Trust Architecture Model requirements: never trust any network other than itself (IACS network).
The BOD offers IACS/OT systems the ability to have their own schedule (different from the IT schedule) due to the nature of, and the design of those systems: Safety of the external physical processes comes first then the availability and integrity of the system to control this physical process. Nothing to do with information! That part is left to the IT group and any “information” should reside on IT networks, not IACS/OT systems networks.
It also offers the IACS/OT Control Systems the ability to determine the vulnerabilities and, per NIST 800–82, define the mitigations of such vulnerabilities, depending on the criticality of the device that shows this vulnerability. NIST RMF is a good tool to use to determine such criticality and therefore help with the mitigation plan or POA&M. Remember though, that gathering an assets list is mandatory and patching or mitigating for all vulnerabilities is also mandatory! Just set a reasonable schedule for doing both and you will be fine. Communicate your security schedule to CISA and they will work with you.
As IACS and most OT Control Systems are part of the Critical Infrastructure, care should be taken prior to communicating the list to CISA and possibly becoming accessible by the public (read potential hackers): an open dialog should be established prior to sharing this vital information regarding the make and model and other pertinent information of those devices. In your division, this information should be saved on the IT network in a “sensitive information” space under strict access control.
For those IT folks who are just learning about IACS, ICS, and OT Control Systems, here is a very simple definition of what constitutes an IACS or ICS:
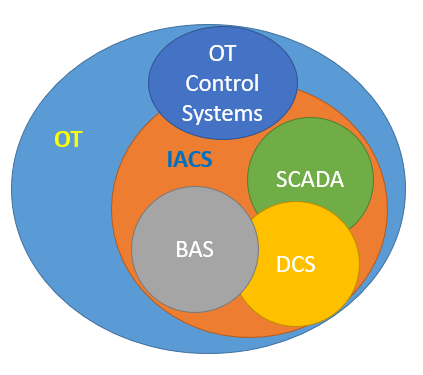
An Industrial Control System (ICS) also referred to as an Industrial Automation and Control System (IACS) is a data system coupled with mechanisms (physical control components) that control flow, and is used to control industrial processes such as manufacturing, product handling, production, distribution, facility environmental controls, physical security, and safety. Industrial automation and control systems include automation controls, supervisory control and data acquisition (SCADA) systems used to control geographically dispersed assets, as well as distributed control systems (DCS) and smaller control systems using programmable logic controllers (PLC) and similar controllers, to control localized processes.
An IACS controls the flow of electricity, fluids, gases, air, traffic, and even people. They are the computer-controlled electro-mechanical systems that ensure installation infrastructure services are delivered, when and where required, to accomplish the mission.
An IACS has the potential to harm humans or animals or to cause sensible/measurable physical damage to property (real property, research equipment, physical research material, etc.), directly or indirectly, as it operates and controls physical processes, including the environment.
Operational Technology (OT) systems are Programmable systems or devices that interact with the physical environment (or manage devices that interact with the physical environment). These systems/devices detect or cause a direct change through the monitoring and/or control of devices, processes, and events.
OT systems include industrial automation and control systems (IACS/ICS), building automation systems (BAS), fire control systems (FCS), and physical access control mechanisms (OT Control Systems), among others.
Please use the methods below if you’d like to learn more about Binding Operational Directive 23–01 or if you’d like to get in touch with us! We’d be happy to help.
Contact Us
contact@hunterstrategy.net






