The Rise of Interlock Ransomware Group

The Interlock ransomware group has rapidly evolved since emerging in September 2024 into a sophisticated threat actor that has claimed 57 victims across critical sectors, including healthcare, education, government, and defense, utilizing advanced techniques like "ClickFix" social engineering and custom malware tools while executing high-impact attacks such as the DaVita breach affecting 200,000+ patients. Most concerning is Interlock's apparent strategic shift from purely financial extortion to potentially state-aligned operations targeting defense contractors and sensitive supply chain infrastructure, suggesting an evolution from cybercriminal activity to geopolitically consequential disruption with national security implications.
Overview
The Interlock ransomware group has rapidly evolved from an obscure threat actor to a sophisticated adversary targeting critical infrastructure across healthcare, education, government, and defense sectors. First emerging in September 2024, Interlock has distinguished itself through multi-stage attack campaigns, strategic targeting, and a destructive combination of data exfiltration and encryption tactics.
Their recent high-profile attack on DaVita Inc., a Fortune 500 healthcare provider serving over 200,000 kidney care patients, marks a significant escalation in both tactical sophistication and strategic intent. This report analyzes Interlock's evolution, technical capabilities, and strategic implications, with particular focus on the DaVita breach and its concerning pivot toward defense contractors with access to sensitive supply chain information.
Key Findings:
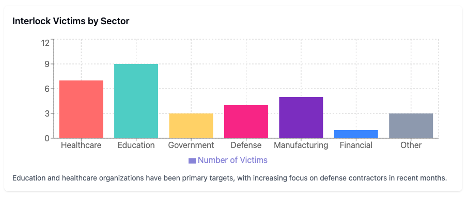
- Interlock has claimed 57 victims across multiple sectors since November 2023, with healthcare and government organizations as primary targets
- Reference Appendix A: Comprehensive Timeline of Interlock Attacks
- The group is executing increasingly sophisticated attacks, including their new "ClickFix" technique and strategic exploitation of weekend operational gaps
- Evidence suggests a shift from purely financial motivation to potentially state-aligned strategic operations, particularly in the defense sector targeting
- The DaVita breach resulted in the exfiltration of 20+ TB of data, affecting hundreds of thousands of patients and triggering significant legal and financial consequences
- Organizations with business relationships to Interlock victims face elevated supply chain attack risk
1. Interlock Ransomware Group
1.1 Timeline and Development
Interlock first surfaced in September 2024, initially employing relatively standard ransomware tactics but quickly distinguishing itself through operational discipline and selective targeting. By late 2024, the group had refined its methodology to include:
- Double extortion (data theft + encryption)
- Multi-stage attack chains
- Strategic targeting of critical infrastructure
- Weekend deployments to minimize detection
- Sophisticated data exfiltration techniques
- Public leak extortion via "Worldwide Secrets Blog"
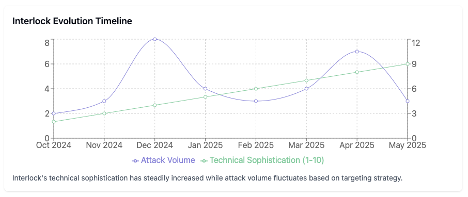
While initially opportunistic in their victim selection, Interlock has demonstrated a clear shift toward sectors with high-value data and critical operational requirements. Their progression from generic ransomware tactics to methodical, high-impact campaigns suggests a maturing operational capability.
1.2 Technical Profile - Ransomware Characteristics Overview
- Custom malware appending the .interlock file extension to encrypted files
- Cross-platform capability targeting Windows, Linux, and FreeBSD systems
- Leverages the LibTomCrypt cryptographic library
- Windows variant uses Cipher Block Chaining (CBC) encryption
- Linux variant employs either CBC or RSA encryption
- Systematically excludes critical system files to maintain an operational environment
1.3 Infrastructure and Operations Overview
- Operational model appears distinct from typical RaaS (Ransomware-as-a-Service) affiliates
- Maintains sophisticated data leak site "Worldwide Secrets Blog" on the dark web
- Uses .interlock@2mail[.]co for victim communications
- Demonstrates operational security awareness throughout the attack lifecycle
- Evidence suggests potential ties to Rhysida ransomware and Vice Society groups
Ransomware Groups Comparison Chart
Detailed Analysis: Interlock, Rhysida & Vice Society
| Characteristic | INTERLOCK | RHYSIDA | VICE SOCIETY |
|---|---|---|---|
| First Observed | September 2024 | May 2023 | June 2021 |
| Operational Model | Ransomware-as-a-Service (RaaS) | Ransomware-as-a-Service (RaaS) | Initially not RaaS Later evolved to use various payloads |
| File Extension | .interlock | .rhysida |
.v-society
.v-s0ciety Multiple commodity extensions |
| Primary Target Sectors | Healthcare Education Government Defense Manufacturing | Healthcare Education Government Manufacturing IT |
Education (Primary) Healthcare Manufacturing Government |
| Geographic Focus |
|
|
|
| Initial Access Methods |
|
|
|
| Malware Tools |
|
|
|
| Encryption Method |
|
|
|
| Extortion Tactics |
|
|
|
| Notable Targets |
|
|
|
| Known Relationships |
Potential ties to Rhysida and Vice Society
|
Strong evidence of ties to Vice Society
Possible evolution of Vice Society operations |
Evidence of connection to multiple ransomware variants
Potential ties to Rhysida |
| Technical Sophistication | Medium to High | Medium | Medium |
1.4 Interlock Characteristics
- The Interlock threat actor group uses its own custom ransomware strain, also called "Interlock." When they successfully compromise systems, files encrypted by this ransomware have the ".interlock" extension appended to them.
- Interlock targets both Windows and Linux systems, utilizing big-game hunting and double-extortion tactics. It not only encrypts data but also exfiltrates sensitive information and threatens to release it unless a ransom is paid.
- MOXFIVE has identified that this group particularly targets organizations in the healthcare sector and has shown a focus on virtual environments. Their tactics involve compromising systems and disrupting operations, with notable features including initiating command-and-control through scheduled tasks over anonymized networks.
- According to Cisco Talos, Interlock shares some similarities with Rhysida ransomware, suggesting that Interlock might have emerged from Rhysida ransomware operators or developers.
- The ransomware affects not only Windows but also the FreeBSD platform and has victimized organizations in the United States and Italy, though it may have hit other countries as well.
- Initially, Interlock used fake browser and VPN client updates to install malware and breach networks. More recently, as of January 2025, they began utilizing a new attack method called "ClickFix" which impersonates IT tools to breach corporate networks.
- Interlock operates under a RaaS model, supplying affiliates with custom ransomware payloads and supporting infrastructure. They maintain a data leak site known as the "Worldwide Secrets Blog" to increase pressure on victims who don't pay.
- Their attacks have a global reach, with confirmed incidents across multiple industries including healthcare, technology, government, and manufacturing sectors.
1.5 Interlock Common Infection Vectors
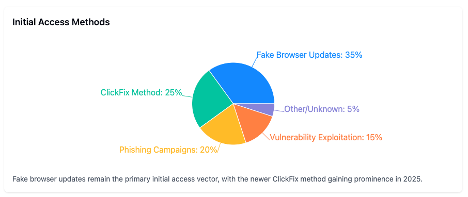
- ClickFix technique: As of January 2025, Interlock began using a new attack method called "ClickFix" which involves impersonating IT tools to breach corporate networks. This represents an evolution in their tactics from their earlier methods of using fake browser and VPN client updates.
- Compromised legitimate websites: Interlock employs a multi-stage attack chain that begins with compromising legitimate websites. These sites then deliver fake software updates, such as Google Chrome or Microsoft Edge installers. When executed, these fake installers deploy a PowerShell backdoor that facilitates the execution of multiple tools, ultimately leading to the ransomware payload.
- Credential stealing: The attack chain includes the deployment of credential stealers and keyloggers before the final ransomware payload is delivered. These tools help attackers harvest authentication credentials for lateral movement and privilege escalation.
- Fake browser updates: Interlock frequently gains initial access through fake browser updaters. In one documented case, the attackers compromised a legitimate news website that prompted victims to download what appeared to be a Google Chrome browser updater. When clicked, this fake updater was downloaded from a second compromised URL of a legitimate retailer.
- PowerShell backdoors: After the initial compromise, typically through a fake updater, attackers leverage various components in their delivery chain, including PowerShell scripts, which serve as backdoors for continued access and execution of malicious activities.
- Remote Desktop Protocol (RDP): For lateral movement within victim networks, Interlock attackers primarily use RDP. They also utilize other remote access tools such as AnyDesk and PuTTY to move laterally and maintain access to compromised systems.
These infection vectors allow Interlock to establish initial access, move laterally through networks, and ultimately deploy their ransomware payload to encrypt files and exfiltrate sensitive data as part of their double-extortion tactics.
1.6 Evolving Tactics
Interlock's infection vectors have evolved significantly since their emergence:
- Initial Phase (2024 Q3-Q4): Primarily leveraged fake browser updates hosted on compromised legitimate websites
- Expansion Phase (2024 Q4-2025 Q1): Added sophisticated PowerShell backdoors and focused on credential theft for lateral movement
- Current Phase (2025 Q1-Q2): Employing the novel "ClickFix" technique impersonating IT tools, alongside more sophisticated tools including: LummaStealer, BerserkStealer and Custom Remote Access Trojans (RATs)
Their lateral movement strategy consistently relies on RDP, AnyDesk, and PuTTY for network traversal and persistence.
Interlock Malware Arsenal Comparison
Technical Analysis: LummaStealer, BerserkStealer & Custom RATs
| Characteristic | LUMMASTEALER | BERSERKSTEALER | CUSTOM RATS |
|---|---|---|---|
| First Observed |
Mid-2024 Adopted by Interlock early 2025 |
Q4 2024 Adopted by Interlock January 2025 |
Multiple generations since October 2024 |
| Programming Language |
Golang (cross-platform capable) |
C++ with modular architecture |
Varies by generation primarily compiled languages |
| Primary Purpose |
Credential and data harvesting
|
Enterprise data exfiltration and monitoring
|
Command and control, persistent access
|
| Target Deployment Phase | Early post-compromise | Mid-campaign on high-value systems | Throughout campaign lifecycle |
| Primary Targets |
|
|
|
| Technical Capabilities |
|
|
1st Gen (Oct-Dec 2024)
2nd Gen (Jan 2025)
ClickFix RAT (Mar 2025+)
|
| Anti-Detection Methods |
|
|
|
| Distribution Vectors |
|
|
|
| Persistence Mechanisms |
|
|
|
| Network Indicators |
|
|
|
| File Indicators |
|
|
|
| Role in Interlock Operations |
|
|
|
| Key Detection Strategies |
|
|
|
2. Case Study: DaVita Inc. Data Breach
2.1 Attack Overview
In April 2025, Interlock executed one of its most significant attacks against DaVita Inc., a Fortune 500 healthcare provider serving over 200,000 kidney care patients across 2,600+ centers in the United States.
Timeline
- Initial compromise likely occurred in early April 2025
- Ransomware deployed on a weekend to exploit reduced IT staffing
- DaVita refused to pay the ransom after two weeks of negotiations
- April 27, 2025: Interlock began leaking stolen data on their dark web site
- As of May 2025: 1.5 TB of sensitive data released with threats to sell 20+ TB more
2.2 Technical Attack Vector Analysis
While DaVita has not publicly disclosed the technical root cause, analysis of Interlock's historical behavior and leaked chat data suggests:
- Initial access via compromised credentials (likely phishing or credential reuse)
- Lateral movement toward on-premise infrastructure, particularly ESXi-based virtual environments
- Systematic data exfiltration before encryption
- Weekend deployment to evade detection and slow down response time
- Possible exploitation of unpatched vulnerabilities in virtualization infrastructure
2.3 Exfiltrated Data and Impact
According to Interlock's leak site and subsequent analysis, the stolen data includes:
- Patient records containing PII/PHI
- Insurance documentation
- User account details and internal credentials
- SQL databases with over 200 million rows of structured data
- Financial information related to vendor transactions
- Operational records and internal communications
Business Impact
- 3% stock price drop following breach disclosure
- Two class-action lawsuits filed against DaVita
- Patient care disruption mitigated through contingency measures
- Ongoing compliance and regulatory investigations
- Reputational damage in a highly competitive healthcare market
DaVita's critical role in U.S. healthcare infrastructure made it an attractive target due to:
- Urgent service continuity requirements (life-saving treatment cannot pause)
- High sensitivity of data
- Limited tolerance for prolonged outages
- Complex regulatory environment
3. Strategic Pivot: Targeting Defense Contractors
3.1 AMTEC/National Defense Corporation Breach
The May 2025 breach of AMTEC (a subsidiary of National Defense Corporation) marks a significant and concerning evolution in Interlock's targeting strategy.
Attack Methodology
- Initial access through phishing campaigns impersonating logistics vendors
- Exploitation of unpatched CVE-2024-21407 (Windows Kernel privilege escalation flaw)
- Credential harvesting using Mimikatz
- Lateral movement across contractor networks
- Exfiltration of highly sensitive defense-related data
Compromised Data
- Classified U.S. Department of Defense materials
- Shipment schedules and logistics information
- Engineering blueprints for military systems
- Internal records linked to contracts with:
- Raytheon
- SpaceX
- Thales
- Foreign defense ministries
3.2 Strategic Implications
This breach represents a potential shift from financially motivated cybercrime to operations with geopolitical significance. The targeting of defense contractors and exfiltration of supply chain data suggests:
- Possible nation-state alignment or tasking
- Interest in military operational intelligence
- Strategic rather than purely financial motivation
- Potential for follow-on supply chain attacks
- Intelligence collection objectives beyond immediate financial gain
Organizations in the defense industrial base with connections to compromised contractors should consider themselves at elevated risk of secondary targeting.
4. Threat Intelligence Assessment
4.1 Attack Pattern Analysis
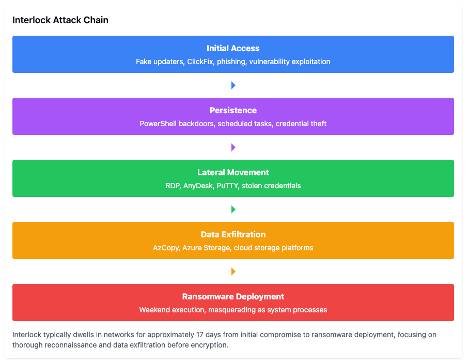
Interlock's operations follow a discernible pattern:
- Initial Access
- Phishing campaigns with industry-specific lures
- Compromised legitimate websites serving fake updates
- "ClickFix" social engineering technique
- Exploitation of public-facing vulnerabilities (e.g., CVE-2024-21407)
- Execution and Persistence
- PowerShell backdoors for initial foothold
- Deployment of custom and commodity info-stealers
- Living-off-the-land techniques to evade detection
- Scheduled tasks for persistence
- Lateral Movement
- Heavy reliance on RDP for network traversal
- Credential theft and privilege escalation
- Use of legitimate administrative tools (AnyDesk, PuTTY)
- Targeting of ESXi-based virtual environments
- Data Exfiltration
- Cloud storage services for data staging
- Azure Storage Explorer and AzCopy for exfiltration
- Systematic collection of high-value data
- Careful operational security during the collection phase
- Impact
- Deployment of custom ransomware (primarily weekend execution)
- Dual encryption approach (file encryption + VMware disk encryption)
- Strategic timing to maximize recovery difficulty
- Post-compromise extortion via dark web leak site
4.2 Victim Targeting Analysis
Interlock has demonstrated both opportunistic and strategic targeting patterns
Distribution of Attacks by Sector (2024-2025)
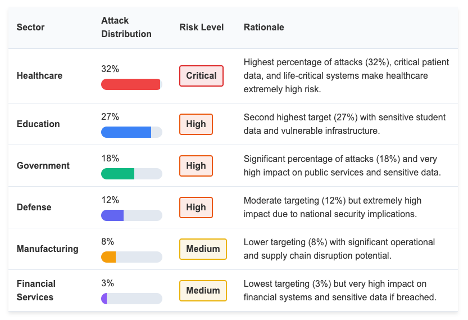
Notable Targeting Patterns
- Preference for organizations with time-sensitive operations
- Focus on entities with regulatory compliance requirements
- Increasing interest in the defense supply chain
- Strategic targeting of weekend operational gaps
- Selection of victims with potential access to partner networks
While there isn't explicit statistical data on the exact probability, there is evidence suggesting Interlock has begun to exploit supply chain relationships and target associated companies, particularly in certain sectors:
Recent reporting indicates that Interlock has "escalated its focus on defense contractors and their supply chains," which puts related companies at risk. The breach of defense contractors like AMTEC and its parent company National Defense Corporation (NDC) exposed sensitive supply chain information that could be leveraged for attacks on partner organizations.
According to Resecurity's analysis, Interlock initially appeared to be opportunistic in its targeting across various sectors, including healthcare, technology, government in the U.S., and manufacturing in Europe." However, this approach "appears to have changed" with a shift toward more strategic targeting of interconnected organizations.
One concerning aspect of the Interlock attacks on defense contractors is that they can expose "intricate supply chain networks." In a recent case, by attacking National Defense Corporation, Interlock "uncovered the details about the supply chains of many other top defense contractors globally who use their products, including their end customers."
This suggests that Interlock is evolving its tactics from purely opportunistic targeting to more strategic approaches that leverage supply chain relationships, especially in high-value sectors like defense, healthcare, and government. The group appears to be recognizing the value of supply chain data for identifying new targets with existing trust relationships.
While it's not possible to assign a specific numerical probability, organizations that have business relationships with known Interlock victims should consider themselves at elevated risk, especially if they're in the defense sector or other industries where Interlock has demonstrated particular interest.
4.3 Supply Chain Risk Assessment - Interlock's Evolution
- Evidence of Partner Targeting: The group has demonstrated willingness to leverage information from one breach to target connected organizations
- Defense Supply Chain Focus: Recent attacks explicitly targeted contractors with extensive partner networks
- Data Harvesting Patterns: Exfiltrated data frequently includes supplier/partner information
- Strategic Intelligence Collection: Evidence suggests collection beyond immediate financial motives
Organizations with business relationships to known Interlock victims should consider themselves at elevated risk, particularly those in defense, healthcare, and government sectors.
5. Mitigation and Detection Strategies
Recommended Security Controls to defend against Interlock and similar threats, organizations should:
Reduce Exposure Surface
- Implement rigorous patch management for known vulnerabilities
- Restrict administrative access to essential personnel only
- Remove unused employee accounts regularly
- Block remote management tools (AnyDesk, PuTTY) unless business-critical
Enhance Detection Capabilities
- Increase monitoring of weekend/off-hours activity
- Deploy specialized detection for fake software updates
- Monitor for credential harvesting attempts
- Integrate Interlock-specific threat intelligence into security tools
Strengthen Resilience
- Implement Zero Trust architecture
- Ensure 24/7 monitoring and response capabilities
- Conduct regular incident response exercises
- Develop and test business continuity plans
Supply Chain Security
- Assess security posture of critical vendors
- Implement network segmentation for third-party connections
- Develop plans for responding to partner breaches
- Share threat intelligence with trusted partners
6. Future Threat Projections
Based on current trends, we anticipate Interlock will continue to evolve in several key areas:
Expanded Social Engineering Tactics
- Refinement of "ClickFix" and similar techniques
- Increased abuse of trusted relationships
- Sophisticated lures targeting specific industries
Enhanced Technical Capabilities
- More sophisticated modular payloads
- Enhanced evasion techniques
- AI-assisted reconnaissance and targeting
- Diversified initial access methods
Strategic Focus
- Continued targeting of national security infrastructure
- Increased supply chain exploitation
- Selection of victims with geopolitical significance
- Legal threats in ransom notes to maximize compliance through regulatory fear
This evolution represents a concerning shift from financially-motivated extortion to potentially geopolitically consequential disruption.
7. Hunter Insights
Interlock's rapid evolution from an obscure ransomware operator to a sophisticated threat targeting critical sectors represents a significant security challenge. Their attack on DaVita demonstrates both tactical sophistication and strategic intent, while their pivot toward defense contractors suggests potential alignment with nation-state interests.
The Interlock threat actor group deploys its own custom ransomware strain called Interlock ransomware, which is notable for its cross-platform capability, double extortion tactics, and technical similarities to the Rhysida ransomware family. This technical profile, combined with their operational patterns of weekend targeting, sophisticated social engineering, and supply chain exploitation, creates an advanced persistent threat that requires comprehensive defense-in-depth strategies.
Organizations must enhance their detection capabilities, strengthen resilience measures, and implement proactive supply chain security to mitigate this evolving threat. The combination of technical sophistication and strategic targeting makes Interlock a particularly concerning adversary in today's threat landscape.
Appendix A: Timeline of Interlock Attacks
Interlock Ransomware Attack Analysis
Comprehensive Timeline & Victim Intelligence (December 2024 - May 2025)
Industry Distribution
Attack Timeline by Month
| Date | Victim Organization | Sector | Impact Details |
|---|---|---|---|
| 14-May-25 | Amtec Inc. | Defense | Targeted defense contractor, compromised sensitive defense-related data |
| 14-May-25 | National Defense Corporation | Defense | Exposed confidential defense supply chain details |
| 4-May-25 | Systems in South Korea and Japan | Various | Breached systems in East Asia - international expansion |
| 4-May-25 | Bentley Pontoons | Manufacturing | Compromised shipbuilding company's internal documents |
| 2-May-25 | Fowler Elementary District | Education | Exfiltrated ~400 GB of sensitive student/employee data |
| 30-Apr-25 | Janco Steel Ltd. | Manufacturing | Compromised internal data |
| 27-Apr-25 | DaVita Kidney Care | Healthcare | Major ransomware attack, leaked ~700,000 files including patient data |
| 24-Apr-25 | Madison Elementary School District | Education | Deployed info-stealing malware to extract organizational data |
| 15-Apr-25 | Texas Tech University Health Sciences Center | Healthcare | Compromised data of 1.4+ million patients |
| 6-Apr-25 | Andretti Indoor Karting & Games | Entertainment | Disrupted operations across multiple locations |
| 6-Apr-25 | Doman Building Materials Group | Manufacturing | Compromised internal documents and operational data |
| 3-Apr-25 | Drive Products | Manufacturing | Compromised sensitive company data |
| 3-Apr-25 | Cherokee County School District | Education | Stole 624 GB of data including employee personal data |
| 1-Apr-25 | National Presto Industries | Defense | Compromised data related to defense subsidiary |
| 22-Mar-25 | General Formulations | Manufacturing | Compromised company data |
| 22-Mar-25 | PMA Canada | Retail | Exposed sensitive business information |
| 21-Mar-25 | Aztec Municipal School District | Education | Compromised student and staff data |
| 6-Mar-25 | Hancock Public School | Education | Compromised internal documents |
| 28-Feb-25 | Wayne County, Michigan | Government | Multiple attacks disrupting public administration services |
| 28-Feb-25 | Smeg Group | Manufacturing | Compromised manufacturing data and internal documents |
| 24-Feb-25 | The Siegel Group | Real Estate | Exposed sensitive real estate data |
| 28-Jan-25 | South Dakota Association of Healthcare | Healthcare | Compromised healthcare data |
| 27-Jan-25 | CMS Life Sciences & Healthcare | Healthcare | Exposed sensitive legal and healthcare information |
| 27-Jan-25 | Modern Healthcare | Media | Compromised internal data and publications |
| 25-Dec-24 | McCormick & Priore, P.C. | Legal | Compromised legal documents and client information |
| 19-Dec-24 | State of Indiana | Government | Disrupted public administration services |
| 18-Dec-24 | Texas Tech University - Costa Rica | Education | Compromised educational data |
| 18-Dec-24 | TTUHSC School of Health Professions | Healthcare | Compromised student and faculty data |
| 16-Dec-24 | Heritage Bank - Greater Cincinnati | Financial | Compromised financial data and customer information |
| 16-Dec-24 | Brockton Neighborhood Health Center | Healthcare | Exposed patient data |
| 8-Dec-24 | BCNC | Compromised data related to child and youth services | |
| 5-Dec-24 | RJM Advertising | Marketing | Compromised marketing data and client information |





