
Explore Posts


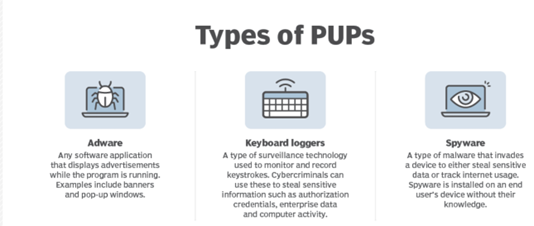
The world of PUP(s) and no, sadly, we are not talking puppies.
Ransomware, which tries to get money from victims by taking over computer home pages. Source…

Strengthening Supply Chain Resilience: CISA’s Hardware Bill of Materials Framework
In a rapidly evolving digital landscape, cyber supply chain security has become a paramount concern for both public and private sectors…

What’s Exploratory Testing?
and Why Should we Use It?

Additive Testing: An Approach to Software Quality
In my last blog post, I discussed my favorite definition of “quality.” In it, I referred to Quality Assurance testers and some types of…

So, What Is Quality?
I have been testing software for a lot of years: first as a power user of software that my company purchased, then as part of my job…

Binding Operational Directive 23-01: Improving Asset Visibility and Vulnerability Detection on Federal Networks
How it applies to Industrial Automation and Control Systems (IACS) and Operational Technology (OT) Control Systems
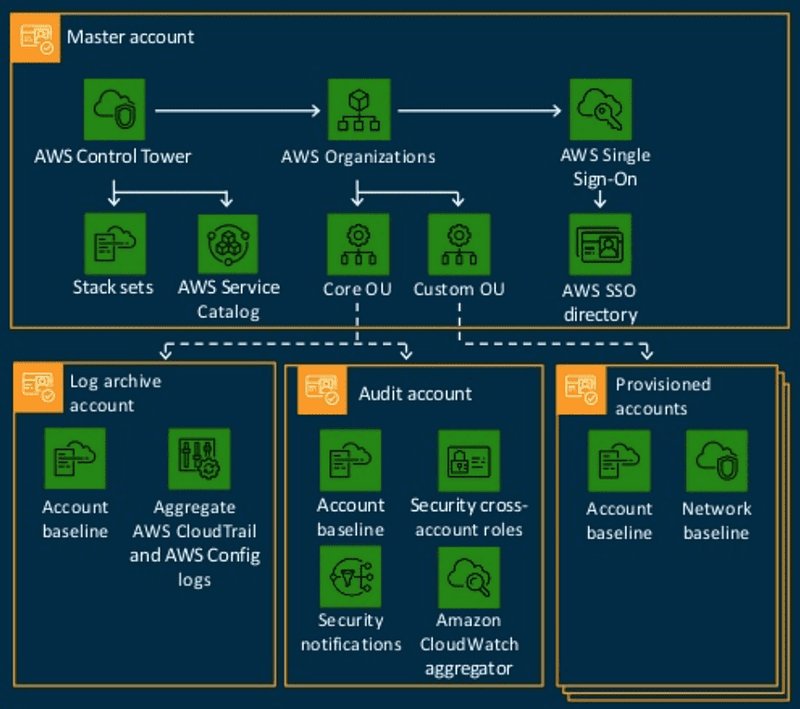
AWS brings Control Tower to GovCloud (US)
Big news in GovCloud came around last week as AWS announced Control Tower support in all GovCloud (US) regions. If this doesn’t seem that…

You may be sharing too much information and not even know it
Today’s threat actors make use of a variety of information to tailor their attacks against organizations and individuals. By collecting…

ICS Antivirus Protection for computer systems on Level 3 and below
When properly deployed and up-to-date, antivirus (AV) software is an important part of a defense-in-depth strategy to guard against…

Industrial Control Systems and Zero Trust Architecture
Industrial Control Systems (ICS) and Operation Technology (OT) Control Systems are computer-based systems used to control physical…
