The World of PUP(s)

The world of PUP(s) and no, sadly, we are not talking puppies.
The beauty that is the Internet, presents us with opportunities as IT professionals to build out our tool stacks. As we grow professionally, so does the tool stack. Even with the best intentions, sometimes in our desire to do better and be better, we lose sight of what is most important…security.
Security does not only entail protecting company assets and resources but also those of the clients we support in the world of cyber security, and yourself as an individual.
As an IT professional, especially an analyst, it is imperative to understand that the best software out there can belie its true intentions. Bad actors can attach malicious software to popular/legitimate programs to deliver malicious payloads, otherwise known as PUPs.
The focus of this post is targeting the analyst audience but is not exclusive to said group. As those at the forefront of protecting our respective companies and the clients we support we must practice what we preach.
“I love being irreverent. But I hate being irrelevant. I love being irreverent because at the end of the day your actions belie your intentions.” — Esai Morales
Irreverence, when it comes security is detrimental to internal and external operations, and when one acts like their intentions are good, their actions indeed belie their intentions.
This leads to the topic at hand, PUP(s). PUP stands for Potentially Unwanted Program(s). PUPs come in many different forms, spyware, adware, and most importantly malware. Often, PUPs are packaged with legitimate software. They are introduced into the environment by the user downloading/installing free software, usually without their knowledge.
In some cases, introduction of malicious software into the environment might not be the user’s intent, their lackluster approach to vetting said software before deployment, could lead to a compromised system and open the door for lateral movement/traversal through the entire network. This is especially pertinent when it comes to SOC operations. As an analyst/security professional it is not only your job to protect yourself by doing the vetting when seeking out free software but also educating and informing your clientele, and their end user base on the subject.
The days of enabling and “kid gloves” approach to users should be well behind us or at the very least limited, especially in today’s environment. On regular basis we see compromised accounts across many cloud providers, rampant ransomware spread (https://www.statista.com/statistics/494947/ransomware-attempts-per-year-worldwide/)and the rise of Threat as-a-Service (for example, https://www.bleepingcomputer.com/news/security/w3ll-phishing-kit-hijacks-thousands-of-microsoft-365-accounts-bypasses-mfa/) and Insider Threat as-a-Service (https://www.forcepoint.com/blog/x-labs/rise-insider-threat-as-a-service).
With those facts and statistics out of the way, let’s get back on track. In many instances security teams and end user bases of any company/organization are the first line of defense when it comes to protecting assets, proprietary information and PII. This is why it is imperative that validation of software requests must be performed through ticket requests, leveraging ITs and security teams’ expertise before issuing approval for deployment.
Recommendations for all involved:
1. Software in question should be vetted by security/IT teams through a thorough review process of the software in question.
2. Said software should be scanned leveraging known tools like Defender and other AV options available to detect any PUPs.
3. Through training and educational initiatives, users should be taught to acquire software from legitimate sources only rather than 3-rd party options. One example would be navigating to https://www.win-rar.[com] for your compression, encryption archiving needs.
4. A better solution would be to ensure the organization has a repo of previously approved and vetted software for users to download and install. This list of software can also be grown through official requests, provided there is a business use-case, via ticket submissions or other channels created specifically for these types of requests.
5. Policies should be in place to dictate user behavior by leveraging AUPs.
6. In certain instances, where the users are empowered to make decisions, here are some additional tips:
a. However inconvenient, installation/licensing agreements should be reviewed prior to installation.
b. If the option exists, use custom installation options to select installing exactly what you intended to install, foregoing other options in the list.
c. Users should still be educated on what to look out for, additional checkboxes during installation prompt should be reviewed as well. People will unwillingly install PUPs simply by being guided by the process itself, where selecting all checkboxes is presented as a necessary part of the installation.
d. Use AVs and other tools that would prevent installation of unwanted software and protect you as the user.
e. This not only applies to regular users but administrators as well, especially administrators and users with elevated privileges. Those of us with higher levels of access should be the standard bearers for expected user behavior and that should trickle down to the rest of the team/organization.
f. Practice what you preach and never abuse your privileges to skirt created processes nor the AUP.
Symptoms of PUPs to look out for:
> Unwanted advertisement pop ups, on occasion even when disconnected from the internet.
> Poor system performance, such as sluggishness, consumption of system resources such as RAM.
> Software being replaced by newer versions of same software without the user’s knowledge or consent.
What do PUPs Do:
> Collect user information, like keystrokes from your keyboard, mouse cursor movements, and browsing history.
> Use the resources of your computer for other purposes, like mining Bitcoin or cryptocurrencies.
> Advertise to you by displaying pop-up windows in your browser. Some particularly malicious PUPs may even redirect your web search results or put ads on pages where there weren’t any ads before.
Source: https://www.pcmatic.com/blog/what-is-pup-malware-and-how-do-you-remove-it/#:~:text=Potentially%20unwanted%20programs%20can%20include,%2C%20branding%2C%20or%20other%20elements. (December 8, 2022 -Nick Buikema)
> Prevent the user from easily uninstalling the software by obscuring the uninstallation process or making it incomplete by leaving traces of itself behind.
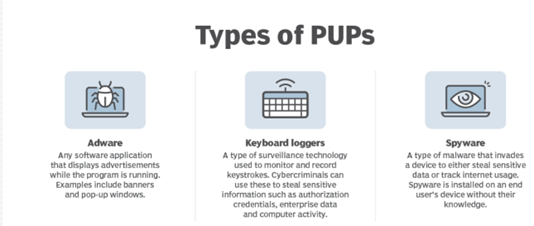
Types of PUPs:
> Browser hijackers, which take control of your web browser settings.
> Spyware, which steals sensitive data and tracks your behavior or Internet usage.
> Adware, which uses pop-up windows, ad banners, and browser toolbars to deliver advertisements straight to your computer.
> Malware, which may do all the above or other things, like steal computer resources.
> Trojans, which pretend to be other viruses, and which often masquerade as freeware.
> Ransomware, which tries to get money from victims by taking over computer home pages.
Source: https://www.pcmatic.com/blog/what-is-pup-malware-and-how-do-you-remove-it/#:~:text=Potentially%20unwanted%20programs%20can%20include,%2C%20branding%2C%20or%20other%20elements. December 8, 2022 -Nick Buikema)
Source: https://www.techtarget.com/searchsecurity/definition/PUP. (Alexander S. Gillis, November 2021)
How do you remove PUPs:
> Although PUPs can be difficult to remove, users can attempt to automatically remove them using antimalware programs or manually remove them.
> If a victim attempts to manually remove a PUP, however, they will have to pay attention more closely. The program may have been created to not delete entirely, for example, or the user may be asked to agree to more terms and conditions that end up downloading another PUP while uninstalling the original program.
> To avoid downloading PUPs in the future, users should pay attention to the terms and conditions when downloading software, as well as the boxes that are selected or unselected. Users can also implement ad blockers that stop ads from appearing or use an antivirus software that protects against PUPs in real time.
Source: https://www.techtarget.com/searchsecurity/definition/PUP. (Alexander S. Gillis, November 2021)
To wrap up, we leave you with this:
Do your part, security starts with you, the user, especially if you are an administrator.
Stay vigilant.
Cybersecurity is a marathon and not a sprint, the work never stops, training, awareness and education are a must.

Contact Us
Contact@hunterstrategy.net